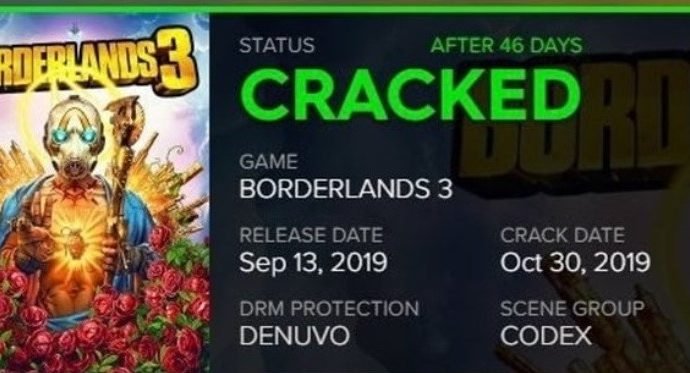
Borderlands 3 hacked a month after its release. Download the cracked version
Even the most sophisticated security measures cannot guarantee the integrity of multiple IT developments, including video games. According to web application security experts, the hacker group known as CODEX hasRead More →