Security researcher MalwareHunterTeam has discovered a new ransomware family that its creators have named Crypton.
After a flood of poorly coded .NET-based ransomware families have invaded VirusTotal, Crypton is a little bit more complex.
“It’s a ‘good’ one,” MalwareHunterTeam told Bleeping Computer on Twitter. “At least compared to the latest .NET ones, this is not bad.”
Crypton infects victims via a generic malware dropper
We currently don’t know how its creators spread this threat, but we know how it infects users. Its operators rely on a malware dropper to gain a foothold on the victim’s computer, should it be via spam or a malvertising campaign.
After infecting the victim, the dropper unpacks and installs Crypton at a later point from a file called crypton.exe. Both the dropper and the ransomware binary have very low detection rates on VirusTotal.
Despite some scanners picking up Crypton by a Hidden Tear variant, MalwareHunterTeam says there are no clues to sustain this labeling.
Files are locked using the dual AES+RSA encryption scheme, also seen in many other top-shelf ransomware families. An AES key is used to lock the files, and the AES key and IV are then encrypted with an RSA public key. The ransomware’s C&C server holds the private RSA key that allows crooks to unlock the user’s files.
Crypton only searches and encrypts the following files.
.xlsx, .cdr, .xls, .vsd, .docx, .doc, .jpg, .pdf, .xml, .dat, .psd, .cd, .txt, .tbb, tbn, .db, .dbx, .pst, .ppt, .pptx, .png, .tiff, .rtf, .htm, .html, .mht, .zip, .rar, .7z, .dbf, .mdbWhen it locks a file, Crypton will append “_crypt” at the end of each file name, leaving the original file extension intact, as such: image.png —> image_crypt.png.
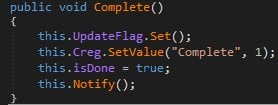
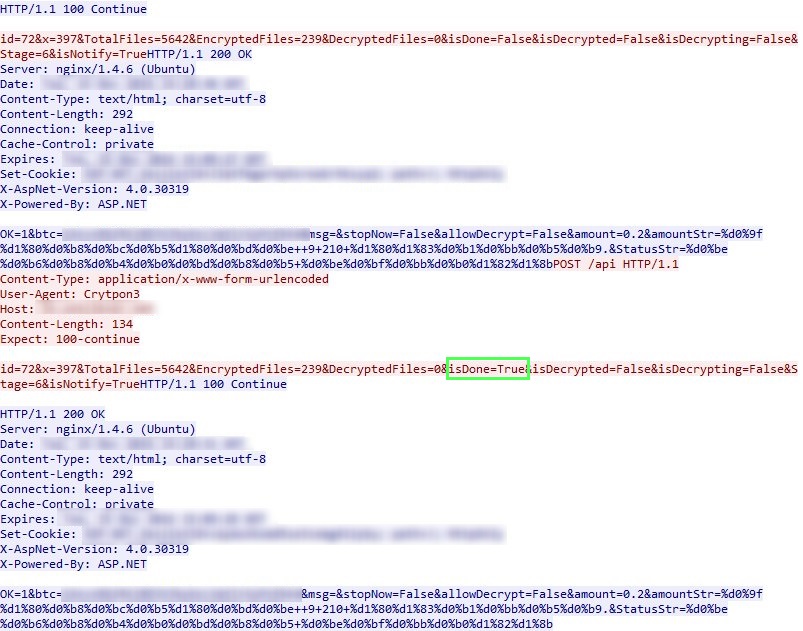
Ever since the ransomware takes root on a system, it constantly pings its C&C server. When the encryption process ends, the ransomware flips the “isDone” flag to true, notifying the crooks that its job has been done.
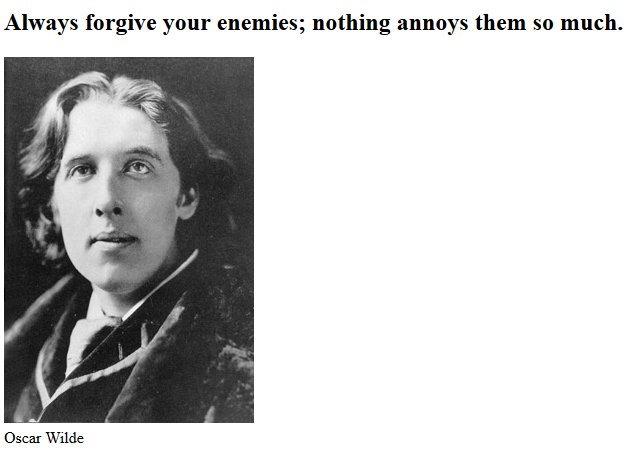
At the time of writing, the C&C server is down. Over the last two days, accessing the server URL yielded an image and quote from Oscar Wilde. This message is now gone, and the URL serves a 404 page.
Once the encryption ends, the ransomware shows the following ransom note, either in English or Russian, depending on the user’s PC language. In the versions recently observed, Crypton asked for ransoms ranging from 0.2 to 2 Bitcoin payment, which is in the $150 – $1,500 range.
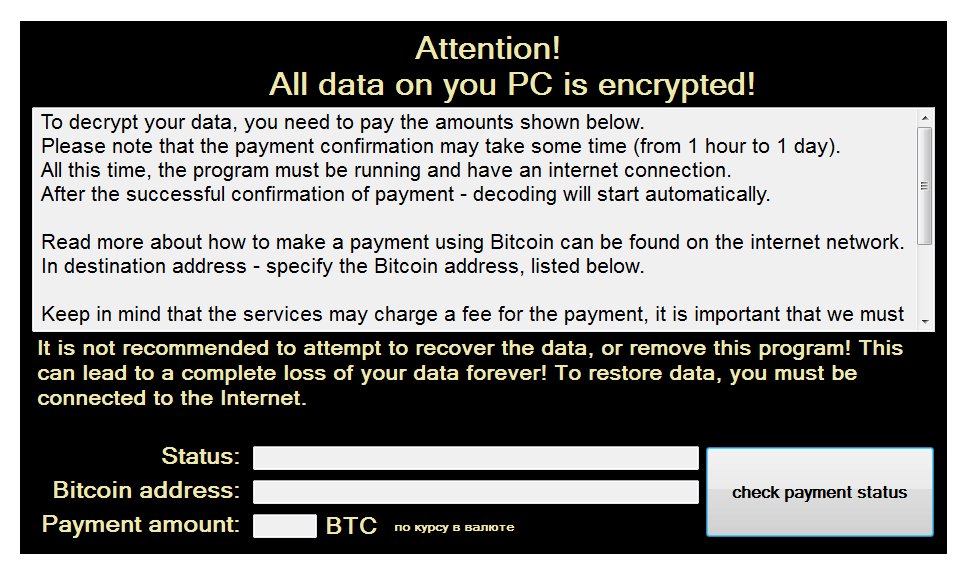

Additionally, the following text, in both English and Russia, is dropped via text files on the victim’s PC.
![]()
At the time of writing, there’s no known method for recovering files locked by Cryption. For assistance with a Crypton infection, please feel free to contact Bleeping Computer experts through our ransomware support forum.
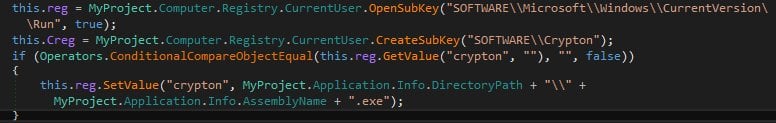
During its installation, Crypton will alter the Windows Registry to gain boot persistence.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











