For almost five years, SecureList researchers reported the identification of an Advanced Persistent Threat (APT) group apparently linked to the infamous Lazarus Group and, unlike other similar groups, with obvious financial motivations, as seen during Bangladesh Central Bank attack back in 2016. Dubbed as BlueNoroff, this group had a huge malicious arsenal, including malware variants, exploits for all sorts of known vulnerabilities, and a large infrastructure at its disposal, and always seemed to be targeting banking networks and electronic transfers systems.
The most recent hacking operation linked to BlueNoroff was identified at the end of 2021, and seems to show that the group has changed targets, focusing this time on the compromise of cryptocurrency exchange platforms via unsuspecting users.
For months, BlueNoroff operators began to closely analyze some virtual asset startups in order to elaborate a complex map of interactions between users and platforms and thus launch an unprecedented social engineering campaign, abusing the trust previously established between the actors of the processes linked to cryptocurrencies.
Experts mention that these attacks could start with a simple notification of a shared document through a friend/co-worker/teammate Google Drive account:
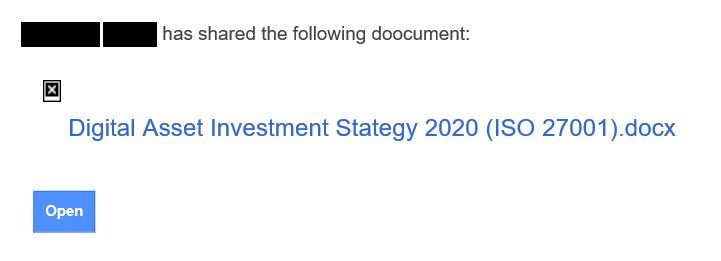
In the example above, we can see an “X” as an icon for an image that could not be uploaded when opening the email on an offline system. If the system had been connected to the internet, there would be an actual icon for a Google document uploaded from a third-party tracking server, immediately notifying the attacker that the potential victim opened the malicious email.
Another variant of the same attack could involve a forwarded email between different users. This attack is more advantageous for hackers, since the original email and forwarded content would seem to have been evaluated by some email security mechanism.
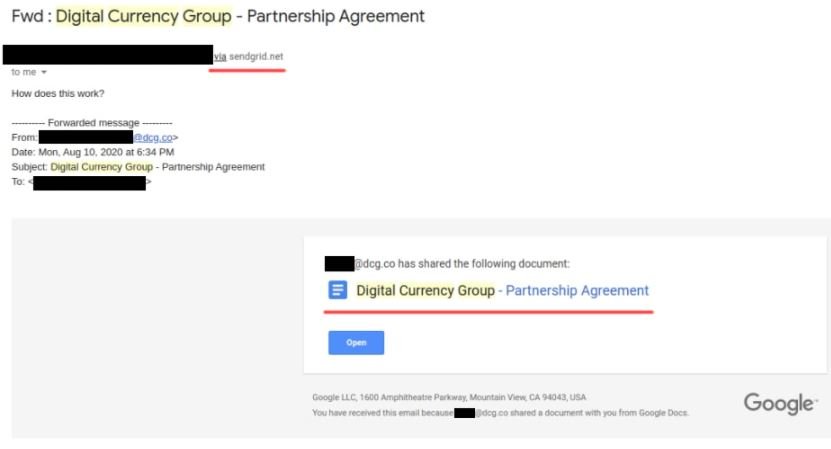
Although the SecureList example does not show the address of the person forwarding the malicious email because it is a real victim, it can be seen that the text reads the web address “sendgrid.net”. Although such a site does not exist in itself, it may be associated with Sendgrid, a firm dedicated to email marketing claims that claims be sending 90 billion emails every month.
Since this is a legitimate business, Gmail accepts the customization of MIME headers, which in turn allows forgery of legitimate emails. In this case, hackers are spoofing communications from the board of directors of Digital Currency Group, a venture capital firm that focuses on the digital currency market.
In addition to Digital Currency Group, BlueNoroff hackers are posing as partners or executives of firms such as Beenos, CoinSquad, Emurgo, Youbi Capital, Global Brain, CoinBig and Secure Digital Markets, as well as other related startups.
In some cases analyzed, hackers have also used compromised accounts on LinkedIn to establish contact with potential victims. This approach allows attackers to operate without drawing too much attention with massive spam campaigns or exploiting dangerous vulnerabilities, keeping a low profile until it’s time to actually attack.
This is not to say that vulnerabilities are not exploited in the process. BlueNoroff usually resorts to the exploitation of CVE-2017-0199 for the automatic execution of a remote script linked to an armed document. A sufficiently trained user could detect suspicious activity, although the attack is highly evasive.

To add another layer of evasion, if the document is opened in an offline environment, the target user will only find informative content on topics related to the attack, possibly taken from trusted sources.
If the entire contents of the document are displayed, a remote template that is another macro-enabled document will be displayed to the target user; the combination of both documents is critical to the attack.
The first of these documents contains two base64-encoded binary objects declared as image data, while the remote template contains a VBA macro that extracts one of these objects and generates a new process in notepad.exe to inject and execute the binary code. While these binaries are identified as JPEG files, they are actually PE files with modified headers.
The successful execution of this content triggers the installation of a malware variant capable of intercepting all kinds of information related to cryptocurrency addresses, access credentials and other data, thus constituting the final stage of the attack.
At the moment the exact scope of the attack is unknown, although it is believed that these malicious emails have been sent to a few thousand users around the world, which could be disastrous for cryptocurrency enthusiasts.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











