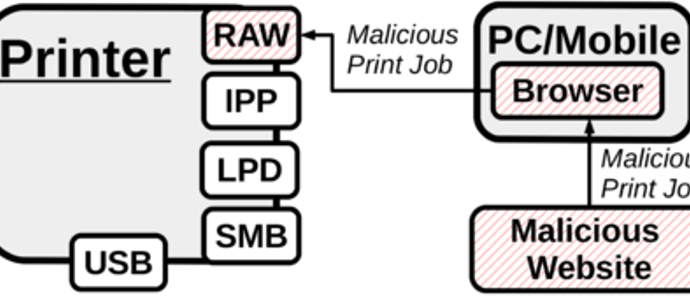
Windows DRM Files Used to Decloak Tor Browser Users
Downloading and trying to open Windows DRM-protected files can deanonymize Tor Browser users and reveal their real IP addresses, security researchers from Hacker House have warned. Attacks using DRM-protected multimediaRead More →