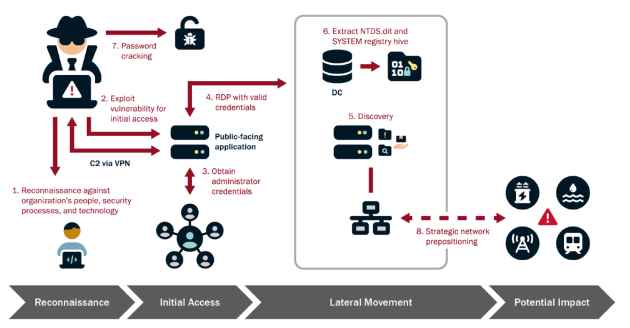
The Looping Attack: Application-Layer Loops as a New DDoS Attack Vector
In the evolving landscape of cybersecurity threats, a new class of Distributed Denial of Service (DDoS) attacks has emerged, exploiting the intricate dance between network services. This phenomenon, known asRead More →