New undetectable technique allows hacking big companies using ChatGPT
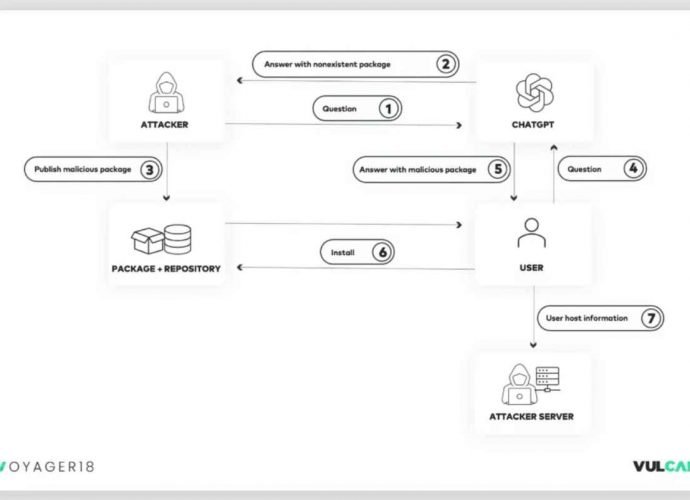
According to the findings of recent study conducted, harmful packages may be readily propagated into development environments with the assistance of ChatGPT, which can be used by attackers. In aRead More →