Facebook and LinkedIn Spam Campaign Spreads Locky Ransomware
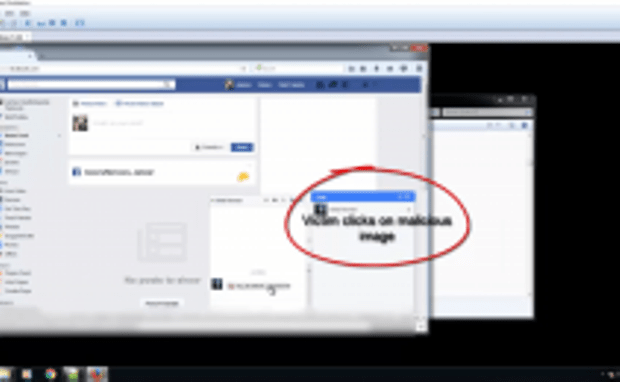
An ongoing spam campaign is using boobytrapped image files to download and infect users with the Locky ransomware, Israeli security firm Check Point reports. aMalware authors are spreading malicious imageRead More →