This ransomware can steal your Veeam credentials and encrypt your backups
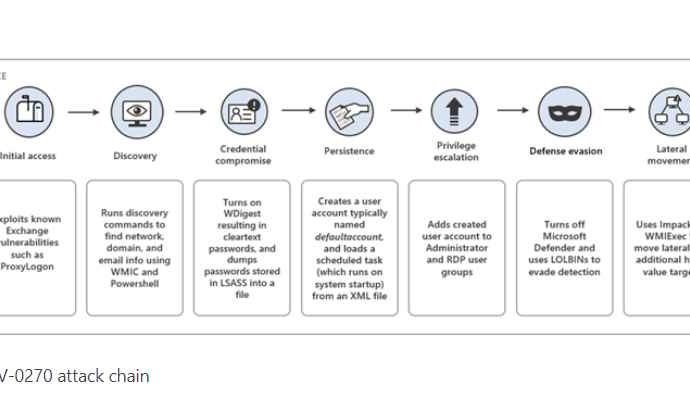
In recent months, hackers utilizing the Noberus (also known as BlackCat, ALPHV) ransomware have been using new techniques, tools, and procedures (TTPs), making the situation even more serious. The usageRead More →