Bypassing pfSense firewall and hacking into application server and firewall itself
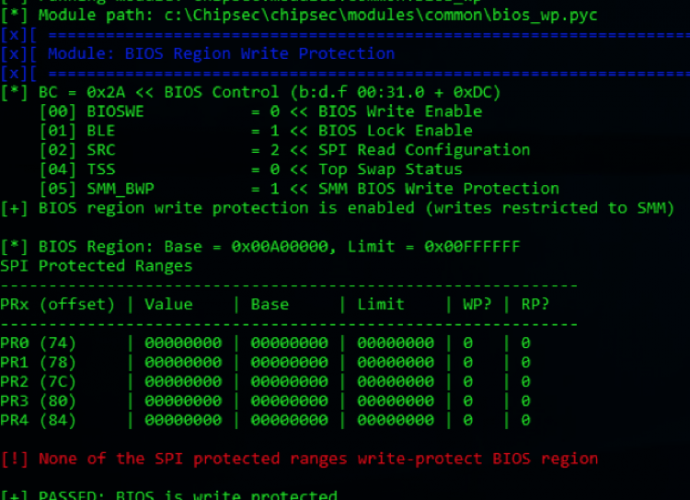
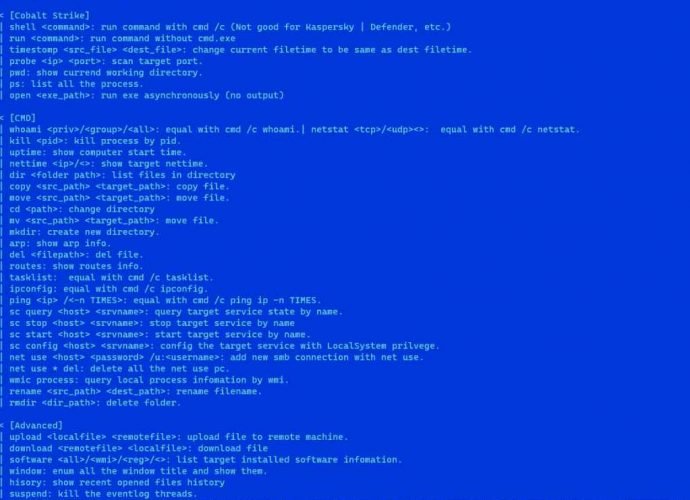
Recent cybersecurity research has unveiled a critical vulnerability impacting over 1,450 pfSense servers, exposing them to potential remote code execution (RCE) attacks. This vulnerability arises from a combination of commandRead More →