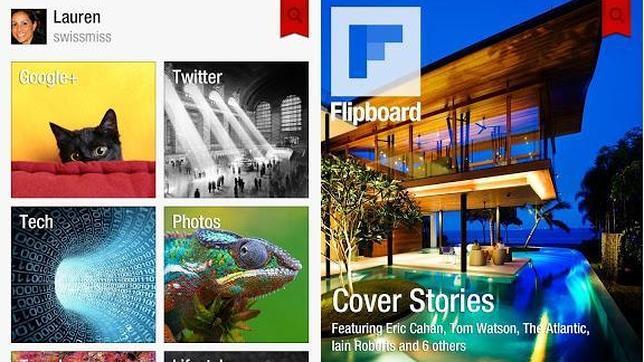
Data breach Flipboard; Hackers commit user Information
A security incident in the Flipboard news application allowed malicious users to access the company’s systems for more than nine months; According to specialists in the IICS’s information security course,Read More →