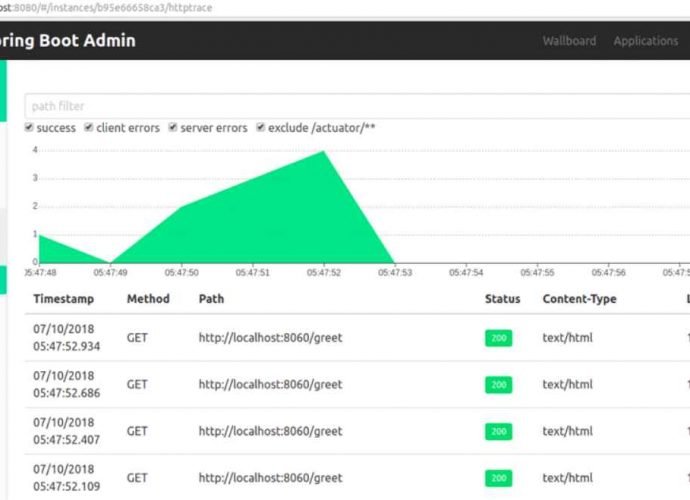
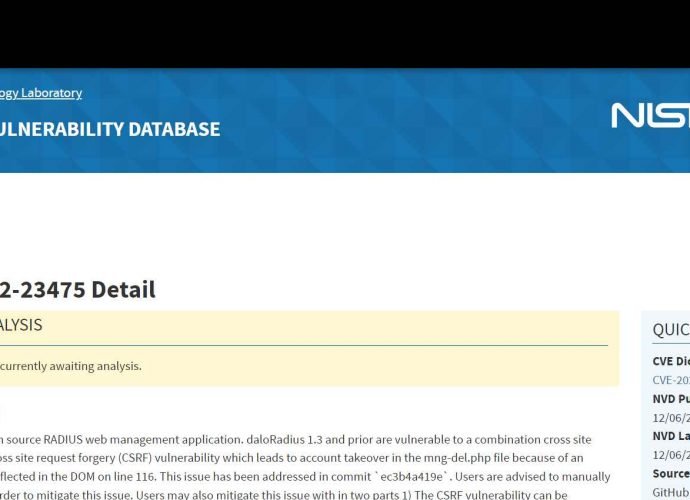
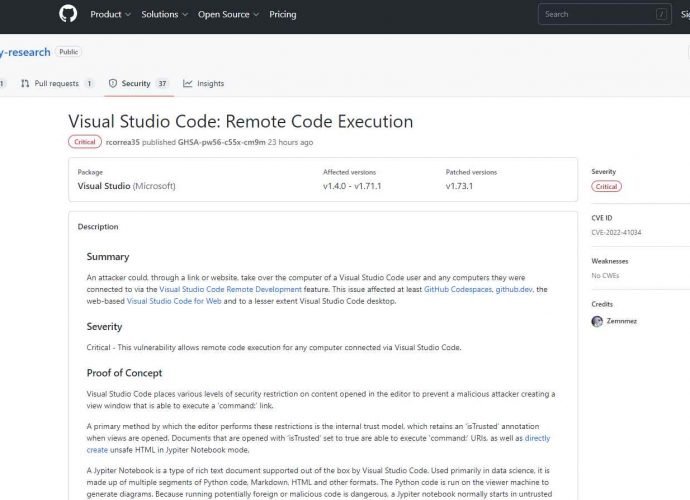
CISA recommends to patch these two Veeam flaws that can be exploited by a remote attacker who is not authenticated to execute arbitrary code
On Tuesday, CISA updated its catalog with five new vulnerabilities, including those that affect products made by Veeam, Fortinet, Microsoft, and Citrix. The previously existing list has been expanded toRead More →