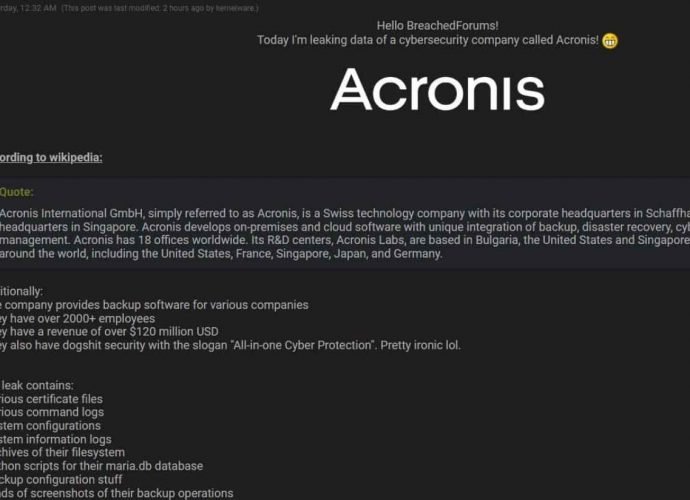
Mispadu Banking Trojan Is Stealing Millions From Victims In Chile, Mexico, Peru And Portugal
Throughout the course of the investigation by researchers, a total of twenty distinct spam campaigns were found to have been directed against the countries of Chile, Mexico, Peru, and Portugal.Read More →