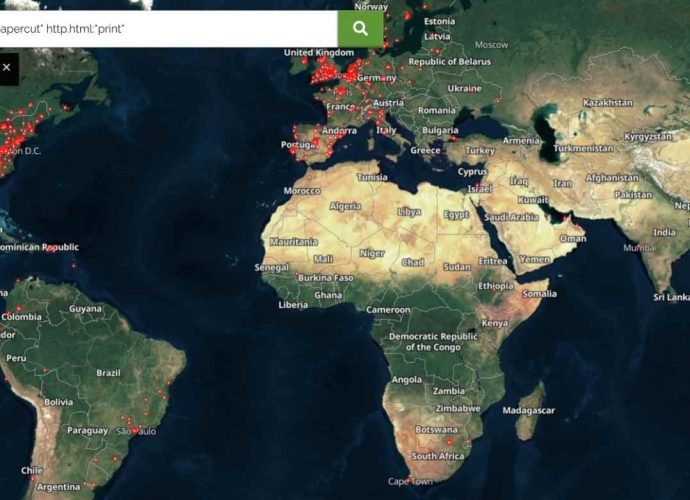
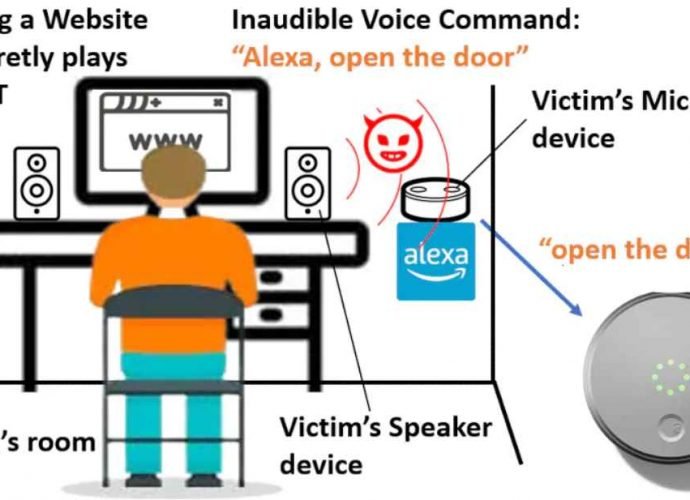
Exploit to hack 100 million users from 70,000 companies using printer software published
The exploit code for a serious flaw in printer software was made accessible to the general public on Monday, as part of a release that has the potential to heightenRead More →