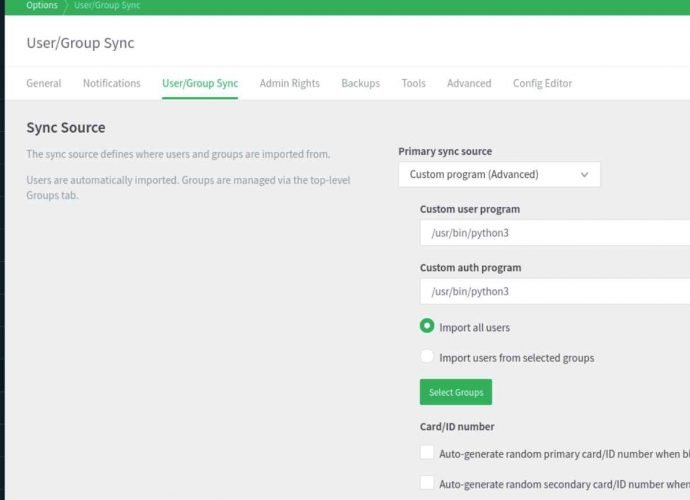
Using NETGEAR’s Nighthawk RAX30 router, hackers can see what you do on Internet
Because IoT devices often have weak security and are easily hacked, the Internet of Things (IoT) has been an increasingly attractive target for cyber assaults in recent years. This is dueRead More →